Terminating bgp with apipa blocks on firewalls -Avoid at all times if you can-
The problem
[Day 1]
Today i got lost in sophos firewalls internal routing and nat labyrinths, what i was trying to do was a simple LDAP integration to a server ath the end of a vpn tunnel. For interoperability reasons with AWS networks, we did used the famous "APIPA" block ip addresses on our bgp neigborship design.
But !
There is catch right, there is always a catch and sometimes a group of catches. Windows server machines won't route or process apipa address ranges. Блять right ? Anyway my options were clear
- Change the addressing on ipsec links
- Snat the requests getting out of the firewall
Here is the topology i was dealing with.
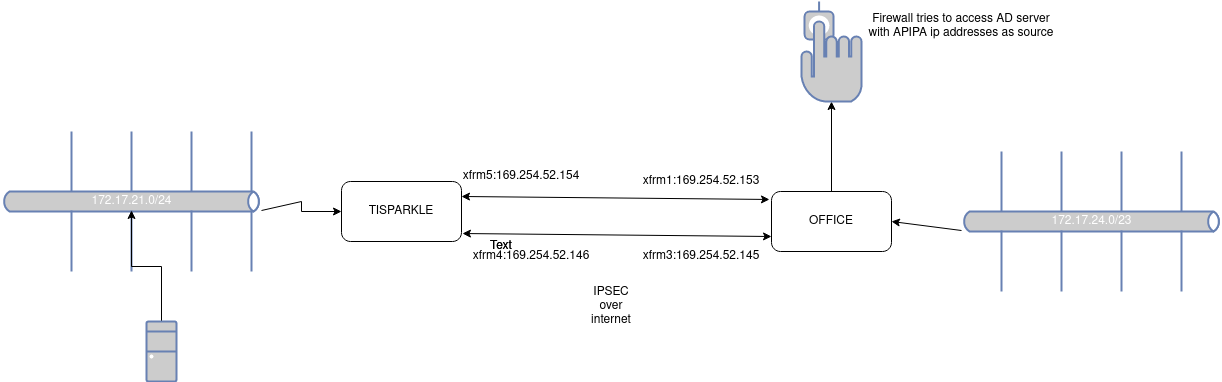
i got close
I thought that amazon must have a sound reason to use these blocks on their integrations. I am sure they never thought the apipa addresses were going to be used as source addresses on production links. Or the CPE's might have limitations too.
I know that Fortigates have the option to specify source addresses for control plane operations, sophos doesn't have them though.
Ok, i can always use the snat option right ? So i went with option 2 on my list.
And after two hours mangling with it i gave up and created a case, which got the required attention immediately from sophos, since the traffic is generated from firewall itself, a special snat entry was not going to be processed as i expect.
Apparently Postrouting operations weren't processed on control plane chains, and i really don't wanted to go with option 2 so a very capable and gentle guy from sophos tried helped me however we couldn't got the golden ticket today !
will update this page on next update i get.
